
Unlocking the Power of Secret Key: A Comprehensive Guide
Are you looking to enhance your GitHub repository’s security? Do you want to ensure that your sensitive data remains protected from unauthorized access? If so, you’ve come to the right place. In this article, we will delve into the world of secret keys, specifically focusing on the “secret key” GitHub file name. We will explore its purpose, implementation, and best practices to help you make the most out of this powerful tool.
Understanding the Secret Key
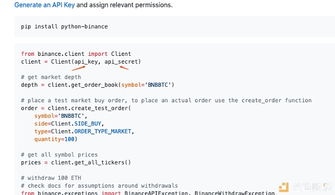
The secret key is a crucial component in the security infrastructure of a GitHub repository. It is a piece of sensitive information that is used to authenticate and authorize requests made to the GitHub API. By using a secret key, you can ensure that only authorized users and applications can access your repository’s data.
When you create a secret key, GitHub generates a unique string that serves as your identifier. This key is then stored in a file named “secret key” within your repository. It is important to keep this file secure and not share it with anyone who should not have access to your repository.
Creating a Secret Key
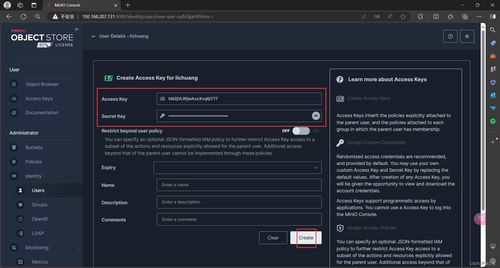
Creating a secret key is a straightforward process. Here’s how you can do it:
- Log in to your GitHub account.
- Navigate to the repository where you want to create the secret key.
- Click on the “Settings” tab.
- Under the “Developer settings” section, click on “Personal access tokens” or “Secrets” (depending on your GitHub plan).
- Click on “Generate new token” or “New secret” to create a new secret key.
- Provide a descriptive name for the token or secret, such as “repository_secret_key” or “api_access_key”.
- Select the appropriate scopes for the token or secret, such as “repo” for read/write access to the repository.
- Click on “Generate token” or “Create secret” to generate the secret key.
- Copy the generated secret key and store it in a secure location.
Using the Secret Key

Once you have created a secret key, you can use it to authenticate requests made to the GitHub API. Here’s an example of how you can use the secret key in a Python script:
import requestsdef get_repository_data(secret_key): headers = { "Authorization": f"token {secret_key}" } response = requests.get("https://api.github.com/user/repos", headers=headers) return response.json() Example usagesecret_key = "your_secret_key_here"repositories = get_repository_data(secret_key)print(repositories) Best Practices for Managing Secret Keys
Managing secret keys is crucial to maintaining the security of your GitHub repository. Here are some best practices to consider:
- Limit Access: Only grant access to the secret key to individuals and applications that require it.
- Regularly Rotate: Change your secret key regularly to minimize the risk of unauthorized access.
- Secure Storage: Store your secret key in a secure location, such as a password manager or a secure environment variable.
- Review Scopes: Ensure that the scopes granted to the secret key are appropriate for its intended use.
- Monitor Activity: Keep an eye on the activity associated with your secret key to detect any suspicious behavior.
Conclusion
In conclusion, the “secret key” GitHub file name is a powerful tool for securing your repository and protecting your sensitive data. By understanding its purpose, implementation, and best practices, you can make the most out of this feature and ensure the safety of your GitHub repository.






