
Unlocking the Power of mimikatz lsadump::sam to File
Have you ever wondered about the capabilities of mimikatz lsadump::sam and how it can be used to file system information? If so, you’re in for a treat. In this article, we’ll delve into the intricacies of mimikatz lsadump::sam, exploring its functionalities, usage, and the benefits it offers. By the end, you’ll have a comprehensive understanding of this powerful tool and how it can be utilized to its fullest potential.
Understanding mimikatz lsadump::sam

mimikatz is a widely-used security tool that allows users to extract credentials from the Windows Security Account Manager (SAM) database. The lsadump::sam command is one of the many commands available within mimikatz, and it is specifically designed to extract information from the SAM database.
When you run the lsadump::sam command, it retrieves a wealth of information, including user names, passwords, and other relevant details stored in the SAM database. This information can be invaluable for security professionals, penetration testers, and anyone else looking to gain a deeper understanding of a system’s security posture.
How to Use mimikatz lsadump::sam to File
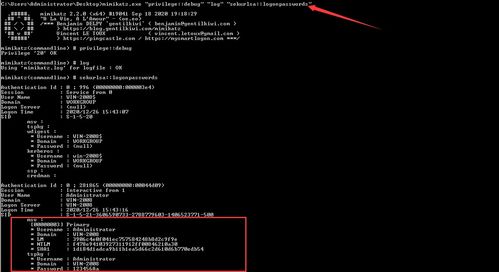
Using mimikatz lsadump::sam to file system information is a straightforward process. Here’s a step-by-step guide to help you get started:
- Download and install mimikatz from the official website.
- Open a command prompt or terminal window.
- Navigate to the directory where mimikatz is installed.
- Run the following command:
mimikatz lsadump::sam /domain:YOURDOMAIN /user:YOURUSERNAME /password:YOURPASSWORD /csv /output:C:pathtooutput.csv - Replace YOURDOMAIN, YOURUSERNAME, and YOURPASSWORD with the appropriate values for your environment.
- Replace C:pathtooutput.csv with the desired location and filename for the output file.
- Press Enter to execute the command.
- The output file will be generated, containing the extracted information from the SAM database.
Benefits of Using mimikatz lsadump::sam to File
There are several benefits to using mimikatz lsadump::sam to file system information:
- Security Assessment: By extracting information from the SAM database, you can identify potential security vulnerabilities and weaknesses in your system.
- Penetration Testing: As a penetration tester, mimikatz lsadump::sam can help you uncover hidden credentials and gain a deeper understanding of a target system’s security posture.
- Forensics: In the event of a security breach, mimikatz lsadump::sam can be used to extract valuable information from the SAM database, aiding in the investigation and recovery process.
- Compliance: Using mimikatz lsadump::sam to file system information can help ensure that your organization complies with relevant security regulations and standards.
Example Output
Below is an example of the output generated by mimikatz lsadump::sam:
| Username | Password | Domain |
|---|---|---|
| admin | password123 | YOURDOMAIN |
| user1 | user1pass | YOURDOMAIN |
Conclusion
mimikatz lsadump::sam is a powerful tool that can be used to extract valuable information from the Windows SAM database. By following the steps outlined in this article, you can easily use mimikatz lsadump::sam to file system information and gain a deeper understanding of your system’s security posture. Whether you’re a security professional, penetration tester, or simply curious about the capabilities of mimikatz, this article has provided you with the knowledge to make the most of




