
Bypass Security Settings Files: A Comprehensive Guide
Security settings files are an essential component of any operating system, ensuring that your device remains protected from unauthorized access and potential threats. However, there may be instances where you need to bypass these settings for legitimate reasons. This guide will delve into the various methods and tools available to bypass security settings files, providing you with a detailed understanding of each approach.
Understanding Security Settings Files
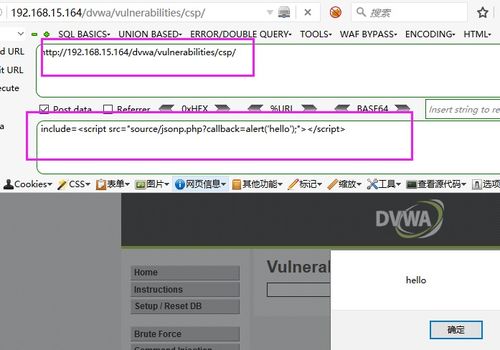
Security settings files, often stored in a configuration file format like XML or JSON, contain rules and permissions that dictate how your device operates. These files are crucial for maintaining the integrity and security of your system. However, there are scenarios where you might need to bypass these settings, such as when troubleshooting or accessing restricted features.
Before diving into the methods to bypass security settings files, it’s important to note that bypassing these settings without a legitimate reason can be risky and may violate the terms of service of your device or software. Proceed with caution and ensure that you have a valid reason for bypassing these settings.
Method 1: Using Command Line Tools

One of the most common methods to bypass security settings files is by utilizing command line tools. These tools allow you to modify system files and configurations directly, giving you the ability to bypass certain restrictions. Here are a few popular command line tools that can be used for this purpose:
| Tool | Description |
|---|---|
| chmod | Changes the file permissions of a file or directory. |
| chown | Changes the ownership of a file or directory. |
| sudo | Executes a command with elevated privileges. |
By using these tools, you can modify the permissions of security settings files, allowing you to access or modify them as needed. However, it’s important to exercise caution when using these tools, as incorrect usage can lead to system instability or security vulnerabilities.
Method 2: Utilizing Third-Party Software
Another method to bypass security settings files is by using third-party software. These tools are designed to modify system configurations and permissions, providing you with the ability to bypass certain restrictions. Here are a few popular third-party software options:
| Software | Description |
|---|---|
| System Mechanic | Optimizes system performance and removes unnecessary files. |
| CCleaner | Cleans up unnecessary files and improves system speed. |
| IObit Advanced SystemCare | Boosts system performance and optimizes security settings. |
These tools can help you modify security settings files and other system configurations, allowing you to bypass certain restrictions. However, it’s important to choose reputable software and ensure that it is compatible with your operating system and device.
Method 3: Editing Configuration Files Manually
For those who prefer a more hands-on approach, editing configuration files manually can be an effective method to bypass security settings files. This method requires a good understanding of the file format and the specific settings you want to modify. Here’s a step-by-step guide on how to do this:
- Locate the security settings file you want to modify. This file is often stored in a specific directory, such as /etc or /usr/local/etc.
- Open the file using a text editor with administrative privileges.
- Identify the specific settings you want to modify and make the necessary changes.
- Save the file and exit the text editor.
- Restart your device to apply the changes.
Editing configuration files manually can be risky, as incorrect changes can lead to system instability or security vulnerabilities. Ensure that you have a backup of the original file before making any modifications.
Method 4: Using Root or Administrator Privileges
Rooting or gaining administrator privileges on your device can provide you with the necessary access to bypass security settings files. This






