Security Onion Linux Distro ISO File Download: A Comprehensive Guide
Are you looking to enhance your network security with a powerful and comprehensive solution? Look no further than Security Onion, a Linux distribution designed specifically for intrusion detection and prevention. In this article, we will delve into the details of downloading the Security Onion ISO file, exploring its features, installation process, and the benefits it offers to both beginners and advanced users alike.
Understanding Security Onion

Security Onion is a free and open-source platform that combines several open-source security tools into a single, easy-to-use interface. It is designed to help organizations monitor their networks for suspicious activity and potential threats. By integrating tools like Snort, Suricata, and Bro, Security Onion provides a comprehensive solution for network security.
Downloading the Security Onion ISO File
Obtaining the Security Onion ISO file is the first step in setting up your network security platform. Here’s how you can download it:
- Visit the official Security Onion website at https://www.securityonion.net/.
- On the homepage, navigate to the “Download” section.
- Select the appropriate version of Security Onion for your needs. The latest version is recommended for the best features and security updates.
- Choose the ISO file format, which is suitable for burning to a CD or USB drive.
- Click on the download link to start the download process.
Once the download is complete, you can proceed with the installation process.
Installation Process
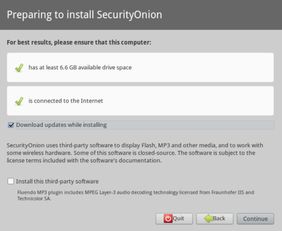
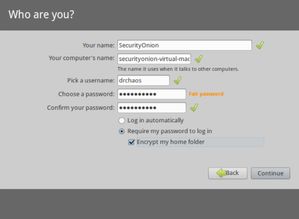
Installing Security Onion is a straightforward process. Here’s a step-by-step guide:
- Insert the Security Onion ISO file into your computer’s CD or USB drive.
- Restart your computer and boot from the CD or USB drive.
- Follow the on-screen instructions to install Security Onion.
- Select the appropriate language and keyboard layout.
- Choose the installation type. The default option is “Security Onion,” which includes all necessary components.
- Enter the root password and confirm it.
- Select the disk where you want to install Security Onion.
- Wait for the installation process to complete.
After the installation is complete, you can access the Security Onion interface by logging in with the root user and the password you set during the installation process.
Features of Security Onion
Security Onion offers a wide range of features that make it an excellent choice for network security. Here are some of the key features:
- Intrusion Detection and Prevention: Security Onion integrates Snort, Suricata, and Bro to provide comprehensive intrusion detection and prevention capabilities.
- Network Monitoring: The platform allows you to monitor your network traffic in real-time, providing insights into potential threats and suspicious activity.
- Alert Management: Security Onion provides a centralized alert management system, making it easier to identify and respond to potential threats.
- Reporting: The platform offers various reporting options, allowing you to generate detailed reports on network activity and security incidents.
- Customization: Security Onion is highly customizable, allowing you to tailor the platform to your specific needs and requirements.
Benefits of Using Security Onion
Using Security Onion offers several benefits, including:
- Enhanced Security: By monitoring your network traffic and detecting potential threats, Security Onion helps protect your organization from cyber attacks.
- Cost-Effective Solution: As a free and open-source platform, Security Onion is an affordable option for organizations looking to enhance their network security.
- Community Support: Security Onion has a strong and active community, providing support, resources, and updates to users.
- Scalability: The platform is designed to scale, making it suitable for organizations of all sizes.
Conclusion
Security Onion is a powerful and comprehensive network security platform that offers a wide range of features and benefits. By downloading the Security Onion ISO file and following the installation process, you can enhance your organization’s network security and protect against potential threats. With its user-friendly interface and strong community support





