
What File Protocol SSH Uses: A Detailed Overview
Secure Shell (SSH) is a network protocol that enables secure communication between two networked devices. It is widely used for remote login, remote command execution, and secure file transfer. One of the key aspects of SSH is the file protocol it employs. In this article, we will delve into the file protocol used by SSH, its features, and its applications.
Understanding SSH File Transfer Protocol (SFTP)
SSH uses the SSH File Transfer Protocol (SFTP) for secure file transfer. SFTP is a network protocol that provides file transfer capabilities over a secure SSH connection. It is designed to replace the older File Transfer Protocol (FTP) with enhanced security features.
Here are some key points about SFTP:
- Secure Connection: SFTP operates over an encrypted SSH connection, ensuring that all data transferred between the client and server is secure and protected from eavesdropping and tampering.
- File Transfer Capabilities: SFTP supports a wide range of file transfer operations, including uploading, downloading, renaming, deleting, and listing files and directories.
- Authentication: SFTP uses SSH for authentication, allowing users to authenticate themselves using their SSH credentials (username and password or public key authentication).
- Port Usage: SFTP typically uses port 22, the same port used by SSH for remote login. However, it can also use other ports if required.
Comparing SFTP with Other File Transfer Protocols
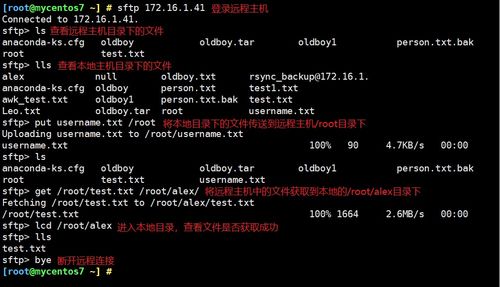
While SFTP is a popular choice for secure file transfer, it is important to understand how it compares with other file transfer protocols, such as FTP and FTPS.
FTP: FTP is an older, less secure file transfer protocol that transmits data in plain text. It does not provide encryption, making it vulnerable to eavesdropping and tampering. SFTP, on the other hand, offers encryption and secure authentication, making it a more secure alternative.
FTPS: FTPS (FTP Secure) is an extension of the FTP protocol that adds encryption and authentication. While FTPS is more secure than plain FTP, it still uses the older FTP protocol and may not offer the same level of security as SFTP.
Applications of SFTP
SFTP is used in various applications, including:
- Remote File Management: SFTP allows users to securely manage files on remote servers, making it ideal for system administrators and IT professionals.
- Web Development: SFTP is commonly used by web developers to transfer files to and from web servers.
- Data Backup and Recovery: SFTP can be used to securely transfer backup files between systems.
- Software Deployment: SFTP is often used to deploy software updates and patches to remote systems.
Table: SFTP vs. FTP vs. FTPS
| Protocol | Encryption | Authentication | Security |
|---|---|---|---|
| SFTP | Yes | Yes | High |
| FTP | No | No | Low |
| FTPS | Yes | Yes | Medium |
In conclusion, SFTP is a secure and versatile file transfer protocol that is widely used for various applications. Its encryption, authentication, and file transfer capabilities make it a preferred choice over less secure alternatives like FTP and FTPS.


